Almost $2 billion lost to BEC scams in 2020
Nearly half of reported cybercrime losses in 2020 were the result of BEC fraud, according to an FBI report
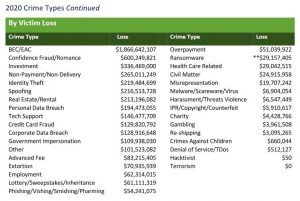
Losses emanating from Business Email Compromise (BEC) and Email Account Compromise (EAC) scams surpassed US$1.86 billion last year, which is more than the combined losses stemming from the next six costliest types of cybercrime in the 2020 Internet Crime Report by the Federal Bureau of Investigation (FBI).
The Bureau’s Internet Crime Complaint Center (IC3) received more than 19,000 reports of BEC/EAC scams last year, a decrease compared to the almost 24,000 incidents reported in 2019. The associated losses, however, increased by over US$90 million and accounted for 45 percent of the total losses (US$4.2 billion).
To illustrate the magnitude of the problem that BEC/EAC scams present, consider that the second costliest cybercrime on the IC3’s list, confidence/romance fraud, registered losses of over US$600 million.
Meanwhile, losses reported from investment fraud were “only” some US$336 million. It bears mentioning that the number of victims more than doubled year-on-year, growing from almost 4,000 to almost 8,800. It’s also generally understood that many types of online crimes and fraud go unreported, so both the number of incidents and the resulting actual losses are very likely to be considerably higher.

Cybercrimes responsible for the greatest financial loss totals (source: IC3, 2020 Internet Crime Report)
One of the key reasons BEC scams remain such a problem is that they are constantly evolving and have become more sophisticated over time, said the FBI. In the past cybercriminals would either hack or spoof the email accounts of chief executives and then use them to request wire transfers to fraudulent bank accounts.
“Over the years, the scam evolved to include compromise of personal emails, compromise of vendor emails, spoofed lawyer email accounts, requests for W-2 information, the targeting of the real estate sector, and fraudulent requests for large amounts of gift cards,” said the Bureau.
BEC targeting various US government organizations
Just days ago, the FBI also issued an advisory about cybercriminals using BEC to target U.S. state, local, tribal and territorial (SLTT) government entities. Over the course of two years, the Bureau observed losses ranging from US$10,000 up to US$4 million, which crippled the operations of SLTT governments and left them strapped for resources. The onset of the COVID-19 pandemic exacerbated problems even further after employees were forced to rapidly transition to remote work.
The cybercriminals used spoofed emails, phishing attacks, vendor email compromise, and various credential harvesting techniques to modify the payment instruction for services rendered by vendors or to alter payroll direct deposit information.
“The substantial amount of publicly available SLTT government operating information required by government transparency requirements enables cyber criminals to acquire information on SLTT leadership, vendor relationships, and associated contractors, allowing them to tailor attacks directly to victims,” the Bureau warned.
In its advisory, the FBI also described several cases where scammers were able to successfully defraud government agencies. In one case, US$1.6 million were lost after a government official received an email with new instructions that came from a legitimate vendor email address. In another case, a small city government received a spoofed email alleging to be from a known contractor requesting a change in payment method, which eventually cost the city US$3 million.
The federal law enforcement agency also shared some advice on how to mitigate the risks of falling for BEC scams:
- Be wary of last-minute changes in payment instructions or a change in the recipient’s account information
- Be suspicious of unexplained urgency concerning payment requests
- If any payment or transaction changes are announced verify them either in person or using a known telephone number
- Contact vendors through numbers that you have on file instead of those sent in emails
- Be on the lookout for grammar and spelling mistakes
- Double-check email addresses and look out for even the slightest changes that could make fraudulent emails look like the real deal