Bandidos at large: A spying campaign in Latin America
ESET Research uncovers an active malicious campaign that uses new versions of old malware, Bandook, to spy on its victims
In 2021 we detected an ongoing campaign targeting corporate networks in Spanish-speaking countries, with 90% of the detections in Venezuela. When comparing the malware used in this campaign with what was previously documented, we found new functionality and changes to this malware, known as Bandook. We also found that this campaign targeting Venezuela, despite being active since at least 2015, has somehow remained undocumented. Given the malware used and the targeted locale, we chose to name this campaign Bandidos.
Bandook is an old remote access trojan: there are references to it being available online as early as 2005, though its use by organized groups was not documented until 2016. The report published that year by EFF, Operation Manul, describes the use of Bandook to target journalists and dissidents in Europe. Then in 2018, Lookout published its research uncovering other espionage campaigns that had different targets but used the same infrastructumre. They gave the name Dark Caracal to the group responsible for the attacks. Finally, Check Point’s report in 2020 showed that the attackers started to use signed executables to target many verticals in various countries.
Previous reports have mentioned that the developers of Bandook might be developers for hire (also known as “malware as a service”), which makes sense given the various campaigns with different targets seen through the years. We must note, however, that in 2021 we have seen only one active campaign: the one targeting Spanish-speaking countries that we document here.
Although we have seen more than 200 detections for the malware droppers in Venezuela in 2021, we have not identified a specific vertical targeted by this malicious campaign. According to our telemetry data, the main interests of the attackers are corporate networks in Venezuela; some in manufacturing companies, others in construction, healthcare, software services, and even retail. Given the capabilities of the malware and the kind of information that is exfiltrated, it seems like the main purpose of these Bandidos is to spy on their victims. Their targets and their method of approaching them is more similar to cybercrime operations than to APT activities such as Operation Manul.
Attack overview
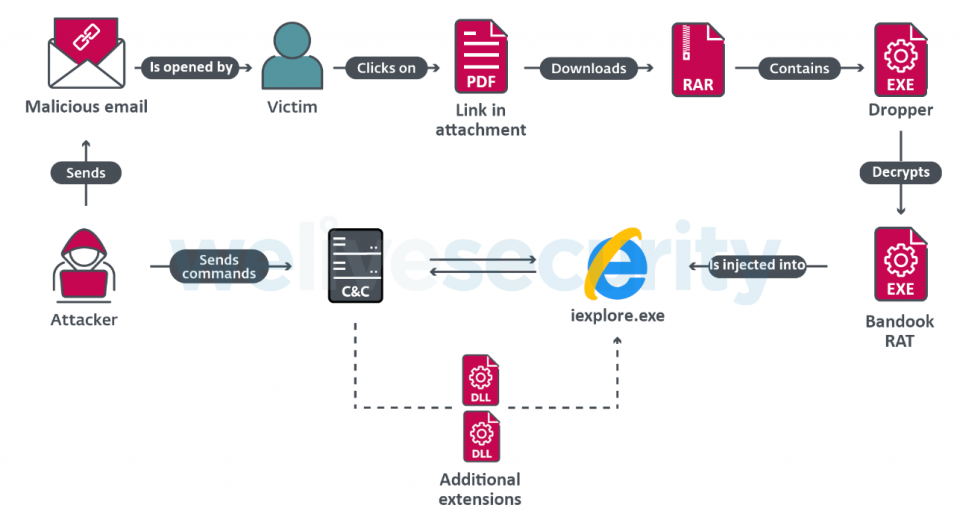
Malicious emails with a PDF attachment are sent to targets. The PDF file contains a link to download a compressed archive and the password to extract it. Inside the archive there is an executable file: a dropper that injects Bandook into an Internet Explorer process. Figure 1 provides an overview of this attack chain.
Emails that contain these attachments are usually short; one example is shown in Figure 2. The phone number at the bottom of the message is a mobile number in Venezuela, though it is unlikely to be related to the attackers.
The attackers use URL shorteners such as Rebrandly or Bitly in their PDF attachments. The shortened URLs redirect to cloud storage services such as Google Cloud Storage, SpiderOak, or pCloud, from where the malware is downloaded.
Figure 3 and Figure 4 are examples of PDFs used in this campaign. The images used in the PDFs are stock images available online.
The content of the PDF files is generic and has been used with various filenames that change between targets. The password for the downloaded archive is 123456.
For a list of URLs used to download the malware please refer to the section Indicators of Compromise (IoCs).
Dropper
Bandook is hybrid Delphi/C++ malware. The dropper is coded in Delphi and is easily recognizable because it stores the payload encrypted and base64 encoded in the resource section of the file. The main purpose of the dropper is to decode, decrypt and run the payload and to make sure that the malware persists in a compromised system. The encryption algorithm was CAST-256 in samples from previous years of this campaign, but changed to GOST in 2021.
When the dropper is executed, it creates four instances of iexplore.exe, where the payload will be injected via process hollowing. Then four entries are created in the Windows registry in HKCUSoftwareMicrosoftWindowsCurrentVersion. The names of the registry keys are based on the process ID (PID) of each of these newly created processes and the values are base64 encoded and contain the path to the dropper, a number to identify different actions, which will be explained later, and another value that isn’t used in the samples that we analyzed. The created keys are shown in Figure 5, along with an example of a decoded value.
Samples from other campaigns follow the same logic, but they use other encryption algorithms.
Payload
When the payload is injected inside the iexplore.exe processes, it will start loading global variables used for various purposes:
- Names for mutexes
- Names for Windows registry keys
- URLs used for:
- C&C communication
- Downloading malicious DLLs
- Parameters to some DLL functions
- Filenames, for example for persistence
- Variables used as parameters for some DLL functions
- Paths for downloaded files
- Payload execution date
Once the payload has finished loading the global variables, it will continue its execution obtaining its injected process’s PID. This PID is used to obtain the base64-encoded data created by the dropper, mentioned above. Once the data is retrieved, the payload will decode it and get the action identifier (see Figure 5) value from it. This value indicates the action it must perform.
Depending on the obtained value, the payload is capable of performing four different actions.
If the value is 0:
- Creates a Windows registry key with the name mep
- Tries to download two DLLs from a URL in the global variables
- Tries to load these DLLs into memory
- Creates different threads to invoke some of these DLLs’ functions
- Starts active communication with the C&C server
If the value is 1:
- Establishes persistence on the victim’s machine; this will be explained in the Registry and persistence section.
If the value is 2:
- Creates a Windows registry key with the name api
- Searches for one of the downloaded DLLs, named dec.dll; if it exists, loads it into memory and calls the export method Init, which creates five folders used for different purposes – for example, save encrypted logs on the Bandook persisted folder mentioned in the Registry and persistence section.
If the value is 3:
- Creates a registry key with the name pim
- Checks whether persistence succeeded; if not, will establish persistence in the folder mentioned in the Registry and persistence section.
Figure 6 depicts a decompilation of this payload-handling code.
Two DLLs can be downloaded from the first action mentioned above or during communication with the C&C server, and they are named dec.dll and dep.dll (the internal name for the first one is capmodule.dll).
dec.dll has a set of functions that enable spying on the victim’s machine. Some of these functions are capable of dropping a malicious Google Chrome extension, and of stealing information from a USB Drive. Meanwhile, dep.dll, which we weren’t able to obtain, has a set of functions that seem to be related to handling files in various formats:
Figure 7 shows part of the decompiled code that loads dec.dll into memory. Figure 8 shows the code related to dep.dll.
Registry and persistence
The payload achieves persistence on the victim’s machine by copying the dropper into a new folder, created by the payload at a path of the form:
%APPDATA%<RANDOM_STRING><RANDOM_STRING>.exe
Both the persisted dropper and the folder use the same name, which is a random string generated by the payload. The screenshot in Figure 9 shows the registry value created by the payload to maintain persistence.
We have also detected other values created by the payload in the Windows registry keys related with its behavior, like: the name used for persistence, a random number used as an ID to identify the victim’s machine, possible filenames (these files can be downloaded by the payload or created by itself), and infection date, among other things.
Table 1 contains the registry entries created by the payload during our analysis, with a brief description of them.
Table 1. Registry entries created by one of the analyzed Bandook samples
| Registry path | Key | Value | Description |
|---|---|---|---|
| HKCUSoftware | der333f | Ixaakiiumcicbcpspmof | Random string used for persistence |
| FDFfda | 5/5/2021 | Compromise date | |
| NVhfhfjs | <RANDOM_NUMBER> | Used to identify the victim’s machine | |
| HKCUSoftwareVBffhdfhf | AMMY132 | <RANDOM_NUMBER>.exe | Related to the export method ExecuteAMMMY from dec.dll |
| gn | <RANDOM_NUMBER>.exe | Related to a new file downloaded during the download of the DLLs, before the connection to the C&C server | |
| idate | 05.05.2021 | Compromise date | |
| mep | 2608 | Process ID from the payload used for the communication with the C&C server | |
| rno1 | <RANDOM_NUMBER>.exe | Can be used to rename a downloaded file through the C&C communication | |
| tvn | <RANDOM_NUMBER>.dce | Related with the export method ExecuteTVNew from dec.dll | |
| api | 2716 | ProcessID from one of the payloads used to install the external DLLs | |
| pim | 2732 | ProcessID from one of the payloads that checks the malware persistence | |
| DRT3 | 1 | Related with the export name ChromeInject from dec.dll |
Other registry locations that can be used to achieve persistence on the victim’s machine are:
- HKCUSoftwareMicrosoftWindows NTCurrentVersionWindows
- HKCUSoftwareMicrosoftWindows NTCurrentVersionWinlogon
Network communication
The communication begins by obtaining the IP address from a domain (d2.ngobmc[.]com) located in the global variables and then establishing a TCP connection to that address with a four-digit port number that changes according to the campaign. Once the payload establishes this connection, it sends basic information from the victim’s machine, like computer name, username, OS version, infection date, and malware version.
After that, the payload will maintain active communication with the C&C server, waiting for commands to execute.
In many cases the information sent to the C&C server is going to be encrypted using the algorithm AES in CFB mode with the key HuZ82K83ad392jVBhr2Au383Pud82AuF, but in other cases the information is sent as cleartext.
The following is an example of the basic information to be exfiltrated to the C&C server, before it is encrypted:
!O12HYV~!2870~!0.0.0.0~!Computer~!Administrator~!Ten~!0d 14h 2m~!0~!5.2~!FB2021~!0~!0~!0~!0~!~!0~!0–~!None~!0~!5/5/2021~!
Of particular interest are the fields:
- !O12HYV: Hardcoded value
- 2870: Victim’s ID generated by the malware
- 0.0.0.0: Victim’s IP address (fake value for privacy reasons)
- Computer: Computer name
- Administrator: Username
- Ten: OS version
- 5.2: Malware version
- FB2021: Campaign ID
- 5/5/2021: Date of compromise
Figure 10 and Figure 11 are Wireshark screenshots displaying two different examples of encrypted and cleartext transmission of information sent to the C&C server.
Regarding the commands that the payload is capable of processing, we found that this sample has 132 commands, although some of these have very similar behaviors. These commands use the following pattern: @<ID> – for example, @0001 – except for the *DJDSR^ command. Depending on the received command, the payload is capable of performing the following actions:
- Obtain information from the victim’s drive units:
- Lists the content of a specific directory:
- File manipulation:
- Take screenshots
- Control the cursor on the victim’s machine:
- Move it to a specific position
- Perform left or right clicks
- Install or uninstall the malicious DLLs (dec.dll or dep.dll)
- Close some connections previously opened by the payload
- Kill running processes or threads
- Pop up a message using MessageBoxA
- Send files to the C&C server
- Invoke DLL functions (dec.dll or dep.dll)
- Windows registry manipulation:
- Check the existence of a registry key or value
- Create a registry key or value
- Delete a registry key or value
- Uninstall the malware
- Download a file from a URL
- Execute downloaded files using the function ShellExecuteW
- Obtain the victim’s public IP address
- Skype program manipulation:
- Stop the process
- Check the existence of the main.db file
- Stops the Teamviewer process and invokes a function from the dec.dll named ExecuteTVNew
- Check for Java being installed on the victim’s machine
- Execute files with extension .pyc or .jar using Python or Java.
Here is a list of what dec.dll is capable of doing on the victim’s machine:
- Chrome browser manipulation
- File manipulation:
- Compress a file
- Split a file
- Search for a file
- Upload a file
- Send files to the C&C server
- USB manipulation
- Get Wi-Fi connections
- Start a shell
- DDoS
- Sign out from Skype
- Manipulate the victim’s screen
- Manipulate the victim’s webcam
- Record sound
- Execute malicious programs
DLL analysis – ChromeInject functionality
When the communication with the C&C server is established, as we mentioned above, the payload downloads dec.dll. We conducted an analysis of one of the most interesting exported methods, named ChromeInject.
This method creates a malicious Chrome extension, by:
- Terminating the chrome.exe process if it is running
- Creating a folder under %APPDATA%OPR
- Creating two files:
- %APPDATA%OPRMain.js
- %APPDATA%OPRManifest.json
- Enabling developer mode of Google Chrome by manipulating the preference file located at:
- %LOCALAPPDATA%GoogleChromeUser DataDefault
- Obtaining the Google Chrome executable path by accessing the registry, in this case it accesses:
- SOFTWAREMicrosoftWindowsCurrentVersionApp Pathschrome.exe
- Launching Google Chrome
- Invoking Windows APIs such as GetForegroundWindow, SetClipboardData, and keybd_event, to load a malicious Chrome extension by simulating a user installation, it:
- Loads chrome://extensions into the clipboard and pastes it by sending Ctrl+V keystrokes
- Sends Tab keystrokes to select the Load unpacked option
- Loads the path to the OPR folder into the clipboard and pastes it by sending Ctrl+V keystrokes
This malicious extension tries to retrieve any credentials that the victim submits to a URL by reading the values inside the form tag before they are sent. These credentials are stored in Chrome’s local storage with the key batata13 and their corresponding URL, where the credentials are sent, with the key batata14. This information is exfiltrated to a different URL located in the global variables of the payload. In our sample this URL was:
https://pronews[.]icu/gtwwfggg/get.php?action=gc1
Figure 12 shows the installed malicious Chrome extension.
Figure 13 and Figure 14 are screenshots respectively displaying the Manifest.json and the Main.js (deobfuscated) source code.
Overlaps and differences with other campaigns
We compared the behavior of our analyzed sample against other posts and documented campaigns like Operation Manul and Dark Caracal and there are some similarities, like:
- The payloads use the same encryption algorithm for communication with the C&C server, AES in CFB mode.
- The encrypted information sent to the C&C server uses the string suffix &&& at the end of it.
- The payloads use the ~! suffix string as a delimiter for the information sent or received.
- Two samples included in the Operation Manul report (SHA-1: ADB7FC1CC9DD76725C1A81C5F17D03DE64F73296 and 916DF5B73B75F03E86C78FC3D19EF5D2DC1B7B92) seem to be connected to the Bandidos campaign, according to our telemetry data. The campaign ID for these samples (January 2015 v3 and JUNE 2015 TEAM) show how far back in time the campaigns go.
- All the samples included in Check Point’s report as “Full Version” in fact target Venezuela and are part of the Bandidos campaign.
- The dropper uses the process hollowing technique to inject the payloads.
We also found some differences, showing changes to the malware over the years, like:
- The dropper, for this campaign, changed its encryption algorithm from CAST-256 to GOST.
- It seems that the malware now has only two DLLs for all its extra functionality instead of the five DLLs mentioned in the Operation Manul report.
- Two new export methods have been added to the dec.dll, named GenerateOfflineDB and RECSCREEN.
- This latest sample contains 132 commands, instead of the 120 commands mentioned in Check Point’s report.
- Unlike the smaller executables described in Check Point’s report, which are signed and seem to be part of a different campaign, these samples are unsigned executables.
- There is a command with the string AVE_MARIA, which could be related to the AVE MARIA (aka Warzone) RAT.
Conclusion
Bandook is a RAT active since 2005. Its involvement in different espionage campaigns, already documented, shows us that it is still a relevant tool for cybercriminals. Also, if we consider the modifications made to the malware over the years, it shows us the interest of cybercriminals to keep using this piece of malware in malicious campaigns, making it more sophisticated and more difficult to detect.
Although there are few documented campaigns in Latin America, such as Machete or Operation Spalax, Venezuela is a country that, due to its geopolitical situation, is a likely target for cyberespionage.
A full and comprehensive list of Indicators of Compromise (IoCs) and samples can be found in our GitHub repository.
For any inquiries, or to make sample submissions related to the subject, contact us at [email protected].
Indicators of Compromise (IoCs)
C&C servers
d1.ngobmc[.]com:7891 – 194.5.250[.]103
d2.ngobmc[.]com:7892 – 194.5.250[.]103
r2.panjo[.]club:7892 – 45.142.214[.]31
pronews[.]icu – 194.36.190[.]73
ladvsa[.]club – 45.142.213[.]108
Samples
| SHA-1 | ESET detection name | Description |
|---|---|---|
| 4B8364271848A9B677F2B4C3AF4FE042991D93DF | PDF/TrojanDownloader.Agent.AMF | Malicious email |
| F384BDD63D3541C45FAD9D82EF7F36F6C380D4DD | PDF/TrojanDownloader.Agent.AMF | Malicious PDF |
| A06665748DF3D4DEF63A4DCBD50917C087F57A27 | PDF/Phishing.F.Gen | Malicious PDF |
| 89F1E932CC37E4515433696E3963BB3163CC4927 | Win32/Bandok.NAT | Dropper |
| 124ABF42098E644D172D9EA69B05AF8EC45D6E49 | Win32/Bandok.NAT | Dropper |
| AF1F08A0D2E0D40E99FCABA6C1C090B093AC0756 | Win32/Bandok.NAT | Dropper |
| 0CB9641A9BF076DBD3BA38369C1C16FCDB104FC2 | Win32/Bandok.NAT | Payload |
| D32E7178127CE9B217E1335D23FAC3963EA73626 | Win32/Bandok.NAT | Payload |
| 5F58FCED5B53D427B29C1796638808D5D0AE39BE | Win32/Bandok.NAT | Payload |
| 1F94A8C5F63C0CA3FCCC1235C5ECBD8504343437 | – | dec.dll (encrypted) |
| 8D2B48D37B2B56C5045BCEE20904BCE991F99272 | JS/Kryptik.ALB | Main.js |
Download URLs
https://rebrand[.]ly/lista-de-precios-2021
https://rebrand[.]ly/lista-de-precios-01
https://rebrand[.]ly/Lista-de-Precios
https://rebrand[.]ly/lista-de-precios-actualizada
https://rebrand[.]ly/Lista-de-precio-1-actualizada
https://rebrand[.]ly/Lista-de-precios-2-actualizada
https://rebrand[.]ly/Precios-Actualizados
https://rebrand[.]ly/recibo-de-pago-mes-03
https://rebrand[.]ly/Factura-001561493
https://rebrand[.]ly/Comunicado_Enero
https://rebrand[.]ly/Comunicado-23943983
https://rebrand[.]ly/Cotizacion-de-productos
https://rebrand[.]ly/informacion_bonos_productividad
https://rebrand[.]ly/aviso-de-cobro
https://bit[.]ly/lista-de-precios2
http://bit[.]ly/2yftKk3
https://bitly[.]com/v-coti_cion03
https://spideroak[.]com/storage/OVPXG4DJMRSXE33BNNPWC5LUN5PTMMZXG4ZTM/shared/1759328-1-1050/Cotizacion nuevas.rar?ad16ce86ca4bb1ff6ff0a7172faf2e05
https://spideroak[.]com/storage/OVPXG4DJMRSXE33BNNPWC5LUN5PTMMRSHA4DA/shared/1744230-1-1028/Lista%20de%20Precios.rar?cd05638af8e76da97e66f1bb77d353eb
https://filedn[.]com/lpBkXnHaBUPzXwEpUriDSr4/Lista_de_precios.rar
https://filedn[.]com/l9nI3nYhBEH5QqSeMUzzhMb/Facturas/Lista_de_Precios.rar
Older C&C servers
d1.p2020[.]club:5670
d2.p2020[.]club:5671
s1.fikofiko[.]top:5672
s2.fikofiko[.]top:5673
s3.fikofiko[.]top:5674
s1.megawoc[.]com:7891
s2.megawoc[.]com:7892
s3.megawoc[.]com:7893
hellofromtheotherside[.]club:6792
medialog[.]top:3806
nahlabahla.hopto[.]org:9005
dianaojeil.hopto[.]org:8021
nathashadarin.hopto[.]org:8022
laraasaker.hopto[.]org:5553
mayataboush.hopto[.]org:5552
jhonny1.hopto[.]org:7401
j2.premiumdns[.]top:7402
j3.newoneok[.]top:9903
p2020[.]xyz
vdsm[.]xyz
www.blueberry2017[.]com
www.watermelon2017[.]com
www.orange2017[.]com
dbclave[.]info
panel.newoneok[.]top
MITRE ATT&CK techniques
Note: This table was built using version 9 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
|---|---|---|---|
| Initial Access | T1566.001 | Phishing: Spearphishing attachment | Bandook operators have used emails with PDF files attached that contain links to download malware. |
| Execution | T1204.001 | User Execution: Malicious Link | Bandook operators have used malicious links to download malware. |
| T1204.002 | User Execution: Malicious File | Bandook operators have attempted to get victims to execute malicious files. | |
| Defense Evasion | T1027 | Obfuscated Files or information | Bandook operators encrypt the payload hidden in the dropper. |
| T1055.012 | Process Injection: Process Hollowing | Bandook operators use process hollowing to inject the payload into legitimate processes. | |
| T1112 | Modify Registry | Bandook operators have attempted to modify registry entries to hide information. | |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run keys / Startup Folder | Bandook operators have attempted to create a Run registry key. | |
| Discovery | T1057 | Process Discovery | Bandook uses Windows API functions to discover running processes on victim’s machines. |
| T1083 | File and Directory Discovery | Bandook operators try to discover files or folders from a specific path. | |
| Collection | T1025 | Data from Removable Media | Bandook operators try to read data from removable media. |
| T0156.001 | Input Capture: Keylogging | Bandook operators may try to capture user keystrokes to obtain credentials. | |
| T1113 | Screen Capture | Bandook can take screenshots from the victim’s machine. | |
| T1123 | Audio Capture | Bandook can record audio from the victim’s machine. | |
| T1125 | Video Capture | Bandook can record video from the webcam. | |
| Command And Control | T1573.001 | Encrypted Channel: Symmetric Cryptography | Bandook uses AES for encrypting C&C communications. |
| Exfiltration | T1041 | Exfiltration Over C2 channel | Bandook exfiltrates information over the same channel used for C&C. |
| T1048.002 | Exfiltration Over Alternative Protocol: Exfiltration Over Asymmetric Encrypted Non-C2 Protocol | Bandook exfiltrates information using a malicious URL via HTTPS. |