Posted inTop News
Is your personal information being abused?
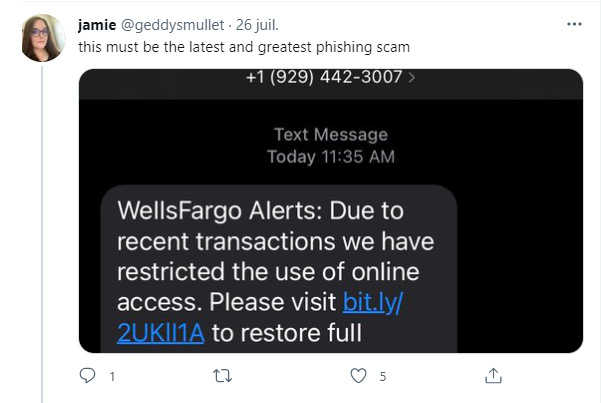
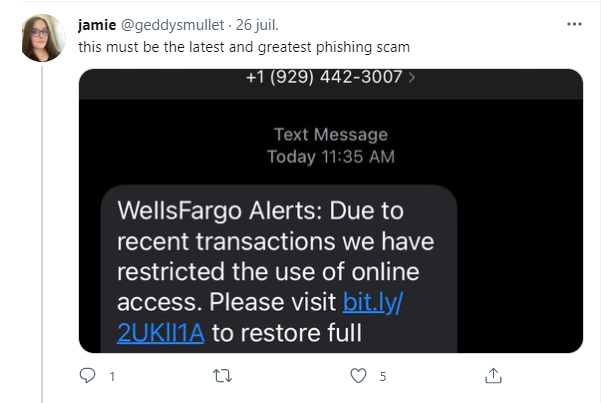
Drowning in spam? A study presented at Black Hat USA 2021 examines if sharing your personal information with major companies contributes to the deluge of nuisance emails, texts and phone calls. Every day my inbox seems to receive more and more spam. Understanding what generates it and how to avoid it is essential in the…