Posted inTop News
Kaseya supply‑chain attack: What we know so far
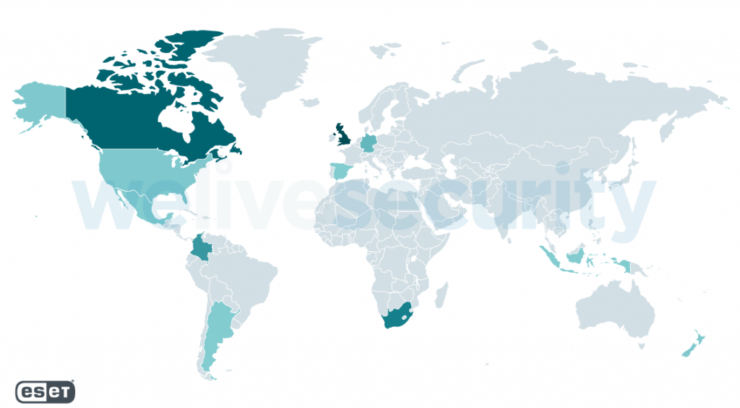
As news breaks about the supply-chain ransomware attack against Kaseya’s IT management software, here’s what we know so far Just when we were getting over the SolarWinds supply-chain attack, we see Kaseya IT management software, commonly used in Managed Service Provider (MSP) environments, hit by another in a series of supply-chain hacks. As with the…