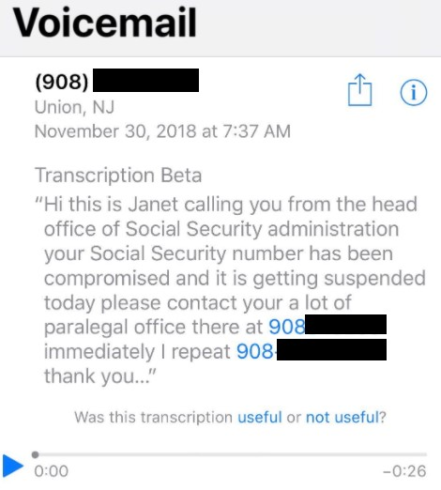
Posted inTop News
In Memoriam: John McAfee
What was it like to work for, and be friends with, the larger-than-life technology entrepreneur back when he helped shape the computer security industry? Editor’s note: The views expressed in this article are solely those of the author and do not necessarily reflect the views of WeLiveSecurity and ESET. This is probably not the first…