Posted inTop News
FBI teams up with ‘Have I Been Pwned’ to alert Emotet victims
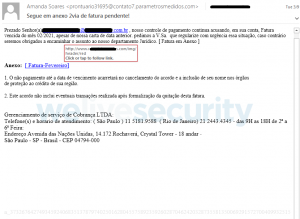
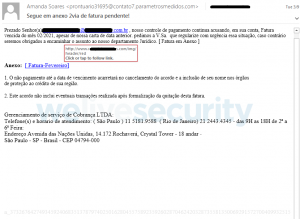
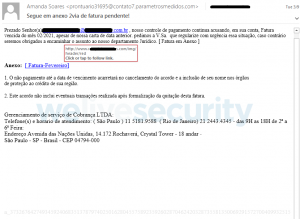
The data breach notification site now allows you to check if your login credentials may have been compromised by Emotet The United States’ Federal Bureau of Investigation (FBI) has shared more than 4.3 million email addresses, harvested by the Emotet botnet, with data breach tracking website Have I Been Pwned (HBIP) in an effort to…