A new paper explains how ransomware has become one of the top cyberthreats of the day and how your organization can avoid becoming the next victim
The infosec community has long been warning that ransomware has the potential to grow into the number one cyberthreat for business. However, since ransom demands were low and malware distribution was a lot less effective a few years ago, many organizations paid those predictions no heed and are now paying large ransoms.
Fast forward to today: with countless reports of ransomware incidents in the media and hundreds of millions of brute-force attacks daily – a common gateway for ransomware – remaining defenseless is no longer an option. In the latest refresh of our popular white paper, Ransomware: A criminal art of malicious code, pressure and manipulation, we explain what led to the worrying increase in severity of ransomware attacks, but also what defenders need to do to keep their organizations out of the danger zone.
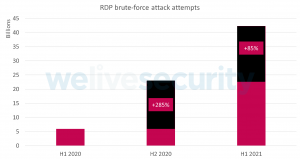
Let’s start with the numbers. Between January 2020 and June 2021, ESET’s brute-force attack protection prevented more than 71 billion attacks against systems with publicly accessible Remote Desktop Protocol (RDP) ports, demonstrating that protocol’s popularity among cybercriminals as an attack surface. While the most notable growth occurred in the first half of 2020, mirroring the lockdowns caused by the global pandemic, the highest daily figures were seen in the first half of 2021.
Figure 1. Number of brute-force attacks has been growing since beginning of 2020, reaching the highest daily figures in H1 2021.
The comparison of H1 2020 and H1 2021 shows an enormous 612% growth of these password-guessing attacks against RDP. The average daily number of unique clients reporting such attacks has also increased significantly, growing from 80,000 in H1 2020 to more than 160,000 (+100%) in H1 2021.
Figure 2. According to ESET telemetry, the detection trend of RDP brute-force attacks shows continuous growth with several large spikes in 2021.
But RDP isn’t the only distribution channel currently being used by the ransomware gangs. Malspam campaigns delivering dodgy documents, malicious macros, harmful hyperlinks, and botnet binaries didn’t go anywhere, and are still bombarding potential victims on top of the billions of brute-force attacks.
Apart from RDP, the rise in ransomware activity has also been fueled by the double extortion (or doxing) technique, pioneered in 2019 by the now-defunct Maze gang. On top of encrypting victims’ data, this infamous ransomware group also started stealing victims’ most valuable and sensitive information and threatened to publish it unless the ransom was paid.
Other ransomware families, including Sodinokibi (aka REvil), Avaddon, DoppelPaymer, and Ryuk, soon followed suit, building upon this effective double-extortion foundation. New methods were introduced targeting not just the victims’ data, but also their websites, employees, business partners, and customers, further increasing the pressure and thus willingness to pay up.
Due to the increased effectiveness of these extortion techniques and a broader range of distribution channels, hundreds of millions of dollars are estimated to have ended up in the accounts of these technically skilled cybercriminals. Shocking ransoms, such as the $70 million demanded by Sodinokibi in the Kaseya attack or the $40 million paid by CNA, demonstrate the scale this problem has reached in 2021.
Large sums flowing into the coffers of ransomware gangs also allow them to develop their ransomware as a service (RaaS) business model and onboard numerous new affiliates. Relieved of the “dirty work” of finding and extorting victims, some of the most advanced actors even started acquiring zero-day vulnerabilities and buying stolen credentials, further expanding the pool of potential victims.
But these threat actors aren’t stopping there. The growing number of ransomware incidents directly or indirectly connected to supply-chain attacks represents another worrying trend that might indicate the direction in which these gangs will head next.
With money, ambition and focus mostly on the side of ransomware gangs, learning from the daily reported nightmare stories and malware analyses has become a must for any IT and security professional. Since the beginning of 2020, it has been demonstrated time and time again that enforced policies, proper configuration of remote access, and strong passwords, combined with multifactor authentication, can be the decisive elements in the fight against ransomware. Many of the incidents named in the Ransomware: A criminal art of malicious code, pressure and manipulation white paper also highlight the importance of timely patching, as known and fixed (but unpatched) vulnerabilities are among the go-to vectors of these gangs.
But even good cyberhygiene and correct settings won’t stop all attackers. To counter ransomware actors who utilize zero-day vulnerabilities, botnets, malspam and other more advanced techniques, additional security technologies are needed. These include a multi-layered endpoint security solution, able to detect and block threats in email, behind hyperlinks, or incoming via RDP and other network protocols; and endpoint detection and response tools to monitor, identify and isolate anomalies and signs of malicious activity in organization’s environment.
New technologies, while bringing benefits to society, also constitute an ever-expanding field of opportunity for cybercriminals. Hopefully, by explaining how serious a threat ransomware has become and what can be done to defend against it, this white paper will help to secure those benefits, while minimizing losses caused by bad actors.